Article first published May 2016, updated July 2019
You can help prevent email fraud, improve your email deliverability, and help ensure continued delivery at receiving mailboxes. Email authentication is the key.
Email authentication isn’t just about security – it’s also about deliverability. By putting DKIM and SPF records in place and authenticating your emails, you can protect your brand and help your emails successfully reach the inbox.
You can help prevent email fraud, improve your email deliverability, and ensure continued delivery. Email authentication is the key.
In this post, we’ll help you understand how email authentication has become an integral part of the delivery process and take a closer look at what happens to an email once you press send.
What is an authenticated email?
As part of the email delivery process, receiving mail servers work to determine the authenticity and legitimacy of your email.
When a mail server receives your email, it basically asks, “Is this email from who it says it’s from? How do I verify that? What do I do if the email is not successfully authenticated?”
Receiving mail servers will also look at the sending reputations associated with the sending domain and sending IP. Content, previous engagement for your sends among their users, and other reputational factors will also factor into whether your email will successfully get delivered to the intended inboxes.
We’ve talked about how you can improve the success of your email campaigns, and how list quality and content factor into your email deliverability.
So, what do we mean when we say an email has been successfully authenticated? In short, that a receiving mail server has checked for the relevant SPF records, the DKIM key associated with your email and sending domain, and that your email has successfully passed those checks.
When sending via Campaign Monitor, SPF records are automatically set up for all clients in Campaign Monitor’s DNS records and it is these records that the receiving mail server will look for.
Your DKIM key is specific to you and is hosted in the DNS records of your domain and as such, putting it in place requires some set up from the domain owner.
Now let’s talk about how a mail server can choose to accept or reject your campaigns based on how it determines the legitimacy and authenticity of your campaigns
Your email might adhere to anti-spam regulations, contain great content and have a send-from address at your registered business domain, but those items may not be enough for a receiving mail server to give it a pass.
What you need to do is authenticate your emails, so that the receiving mail server has verifiable records to check against and say, yes, this email is from Campaign Monitor and not a phisher or a spoofer pretending to be Campaign Monitor.
What does a receiving mail server look for?
The receiving mail server looks for specific items of information in your email (as well as the DNS records of your domain) in order to determine whether the email is legitimate and safe for its users to receive, and then, whether the email is being sent from an authorized source.
DNS stands for Domain Name System. This system is essentially the phone book of the Web that organizes and identifies domains. While a phone book translates a name like “Acme Pizza” into the correct phone number to call, the DNS translates a web address like “www.google.com” into the physical IP address—such as”74.125.19.147″—of the computer hosting that site.
SPF is a mechanism by which a receiving domain can check whether an email has originated from a sending IP that is authorized to send emails on behalf of the admins of a given domain.
When you create an SPF record, you put in place a list of IPs/sending hosts that are authorized to send mail on behalf of your domain.
So, for example, someone attempts to spoof Campaign Monitor by sending an email with a forged send-from address. To a recipient, the email may look legitimate, but the content may be harmful and not from a legitimate source.
With SPF records in place, a receiving mailbox can determine whether the email that appears to be from Campaign Monitor is being sent from an IP that has been authorized for sending by Campaign Monitor.
If the sending IP and sending host match those listed in the SPF record for the send-from domain, the email will have passed SPF-based authentication.
If the email is sent from a sending host or IP that is not in the SPF record for Campaign Monitor, the receiving mail server can determine that the email isn’t coming from an IP authorized and verified by Campaign Monitor and that the email could be illegitimate in nature.
SPF records are added automatically for all clients in Campaign Monitor’s own DNS records. If you already have your own SPF record, be sure to add our details to it.
DKIM is a method of authentication based on adding an encrypted signature to your emails. DKIM is one of the most effective ways to combat abuse, and it can also greatly improve the deliverability of your emails.
To implement DKIM authentication, you need to have access to the DNS records of the sending domain in order to add a DKIM key. This ensures legitimacy as only the domain holder can amend those records, and this is one of the most integral parts of how DKIM functions. Thankfully, while the mechanics behind DKIM are fairly complicated, implementing it is relatively simple.
Once you have DKIM in place in the DNS records of your domain, your emails will be much better positioned to reach the inbox and you will also be helping protect yourself and your users against spam and phishing attempts.
Here’s a whistle-stop tour of how it works:
Once DKIM records are in place and verified, your emails will have a DKIM signature added to the email header upon sending.
This encrypted signature is generated based on the DKIM key that you have added to the DNS records of your domain and a hash string based on elements of the specific email being sent. This means that every one of your emails carries a unique DKIM signature.
When a receiving mail server gets your email, it will decrypt the DKIM signature using the public key that is hosted in your DNS records. It will also simultaneously generate a new hash string based on the same elements of the email that were used when the email was sent.
If the decrypted signature matches the newly generated hash string, then the email successfully passes DKIM authentication.
DKIM authentication means that a receiving mail server can do two things:
- It can safely determine that the owner of the domain (where the DKIM key is) did in fact send the email.
- The receiving mail server can also see that the contents of the email were not changed or modified in transit between the sender and the recipient.
For those reasons, DKIM is the most robust authentication tool in your arsenal and by putting it in place, you ensure the long-term viability and success of email marketing for your brand.
Why you should care about email authentication
The increased importance of email authentication comes as a direct result of the continued use of email as a platform for fraud, spam, and spoofing.
As a result, more robust measures are being taken by ISPs and receiving mailboxes to protect their users from spam and phishing emails. The implementation of more robust policies by ISPs and an increased necessity of authentication for successful delivery is one part of that combined effort.
As more and more ISPs adopt stricter policies, senders without authentication will see difficulties with inbox placement and may find themselves at risk.
Email authentication is as important to the long-term success of your email marketing as the quality of your list or the strength of your design and content.
Email authentication and how to authenticate your domain
All email authentication starts with authenticating your domain. You need to allow your Email Service Providers (ESP), in this case Campaign Monitor, to send emails with permission from your company.
Authentication is done through the DNS records which your company has access to. These records tell your customer’s email servers that the marketing emails you’re sending are safe and from a reputable company.
Receiving an email from an unreliable source is a good way to disengage a customer from your email list. They could block you, report you, and never return to your company again.
How to authenticate your domain on Campaign Monitor
If you’re having issues with spamming and phishing, Campaign Monitor technicians can help troubleshoot your problems. The first step that we take is investigative. We want to make sure that our customer has authenticated their domain first.
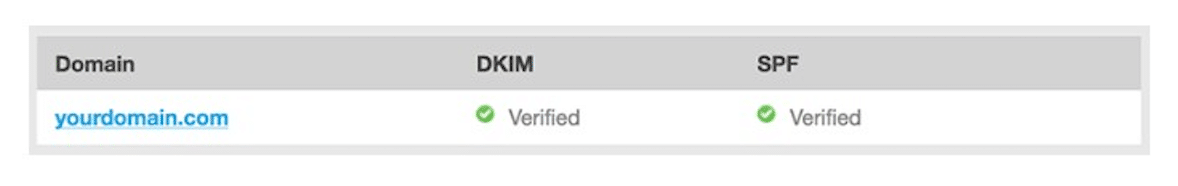
The easiest way to check to see if your domain is authenticated is to go to your Account Settings and click Authentication.
Your screen should say this:
If it turns out that both your DKIM and SPF are not verified, then it’s time to get your domain authenticated. You can do this with the following steps:
- Go to your Account Settings in your Campaign Monitor account
- Click Authentication
- Click Add a sending domain
- Enter your company’s domain name
- Click Generate DNS records
- Add TXT Name and TXT Value to your DNS records
- If using Campaign Monitor, click I’ve added the record, please verify it
After these seven steps are completed and your domain authentication is set up, you can go back to your Account Settings and view your Authentication page. You should now have a verified DKIM and SPF, just like in the picture above.
A note on DKIM keys
It’s important to note that every year your company should update your DKIM keys. This helps combat the potential of fake emails in your customer’s inboxes.
It’s similar to changing the password to your email account or changing the lock on your front door. Extra security and email authentication are a must for the best customer engagement possible.
Another thing to take into consideration is the date of your original DKIM. If it was made before 2013, then you need to change your DKIM key from the old 768-key to the newer version of 1024-keys.
Email authentication and customer engagement
Now you’re ready to send your emails without worrying about the safety of your customer’s information, or your company’s information. Even if you aren’t on the technical side of your company’s email marketing campaign, this information is helpful to know.
It’s also helpful to note that email authentication and customer engagement go hand-in-hand. As an email marketer, you’re on the customer engagement side of the business. So, if you notice things going awry, like your emails getting blacklisted or ignored, then you can take the responsibility of discovering the problem. It will most likely be an authentication issue.
The rundown:
- Demonstrate that your company values reputable engagement by setting up your domain authentication.
- Update your DKIM keys annually for added security to your email campaigns.
- Improve customer engagement by keeping your company and your customers’ emails safe.
Wrap up
By putting email authentication in place, you are mitigating the potential for email fraud targeting your brand and also helping your emails reach your subscribers.
If your email campaigns are not already authenticated, now is the time to make it happen. If you would like more help with email authentication or want to learn more about DNS and DKIM keys, then check out how Campaign Monitor helps their customers troubleshoot problems.